Hi there!,
Today I’d like to share my thoughts about the Microsoft Entra Internet Access feature which is a part of the broader solution called Global Secure Access.
Let me tell you a story…
A long time ago we were living in a world of Covid. We were locked in our homes and most of us were working remotely. It was a difficult time for us as a people and, at the same time, for our IT folks, securing access to the company environment.
We all know that there are companies that are not so optimistic about remote types of work. Someone might think – but we have a VPN”.
VPN is not a security feature, it allows us to connect our device to the corporate network, nothing else…
After 2 years we got our freedom again – lockdown was canceled. we got back to our offices but a hybrid model of work stayed with us.
Solution Overview
Recently Microsoft announced something called Global Secure Access (GSE).
GSE is a part of Microsoft Security Service Edge (SSE) – a solution that links for features:
- Global Secure Access
- Microsoft Entra Internet Access
- Microsoft Entra Private Access
- Microsoft Defender for Cloud Apps (MDAP)
- Conditional Access (CA)
- Continuous access evaluation (CAE)
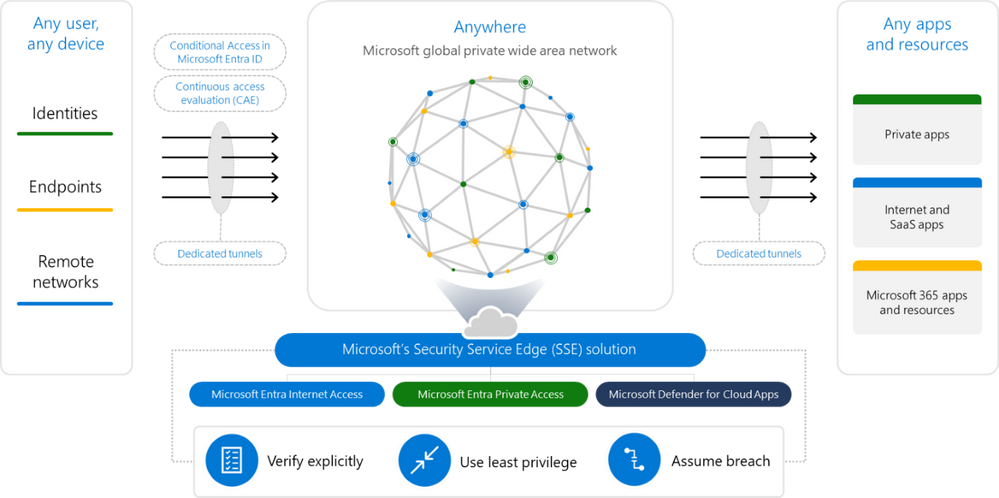
Microsoft Entra Internet Access
Today we will focus on the first part of the puzzle – Microsoft Entra Internet Access
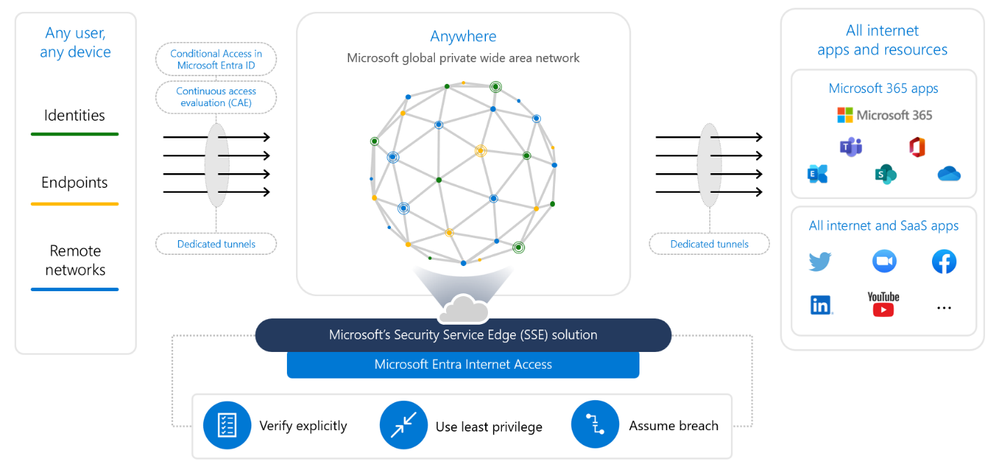
here we need to stop for a while and describe the diagram.
On the left side, we have objects such as identities, endpoints, and remote networks.
On the right side, we have our destination which is M365 apps and Internet / SaaS products
Between them, we have something called tunnels that are built to secure connection to the mentioned destinations.
As a part of the process, we can link CA policies same as CAE to the tunnels to make the tunnel even more secure, and compliant with our conditional access policies.
The whole solution allows us to be compliant with three main ideas from the Zero Trust Model:
- verify explicitly
- use the least privilege
- assume breach
I have mentioned tunnels. This is where Microsoft enables protection for things like:
- universal access controls,
- universal tenant restriction,
- token protection,
- web content filtering,
- cloud firewall,
- threat protection,
- TLS inspection
Setup
Requirements
To use Global Secure Access the following things are needed:
- Microsoft Entra ID Premium P1 license (GSA is a preview feature but it requires this license)
- Windows 10 or 11 device (64-bit OS system)
- Microsoft Entra joined or Microsoft Entra hybrid joined device
- Admin credentials on the workstation.
Implementation
Within this article we will focus on one of two scenarios for Entra Internet Access solution:
- Accessing from workstation
- Accessing from remote networks
Enabling Global Secure Access
To enable Global secure access please use the following link. Below you can find a short video presenting how to enable the feature.
Manage traffic forwarding profiles
The next step is to enable traffic forwarding profiles.
Tenant Restrictions
The video below presents tenant restriction configuration
Global Secure Access Signaling and Conditional Access
Next on the list is to configure global secure access signaling and conditional access.
Client Installation
Last but not least is global secure access client installation
To do that we have to download the GSA agent by going to this link.
Installation is very simple but you have to remember two things:
- make it on Microsoft Entra joined or Microsoft Entra hybrid joined devi
- It works only on Windows 10/11 devices
After installation, it is worth checking the Client Checker tool by clicking on the icon and selecting Client Checker. We will be able to check if the configuration works properly.
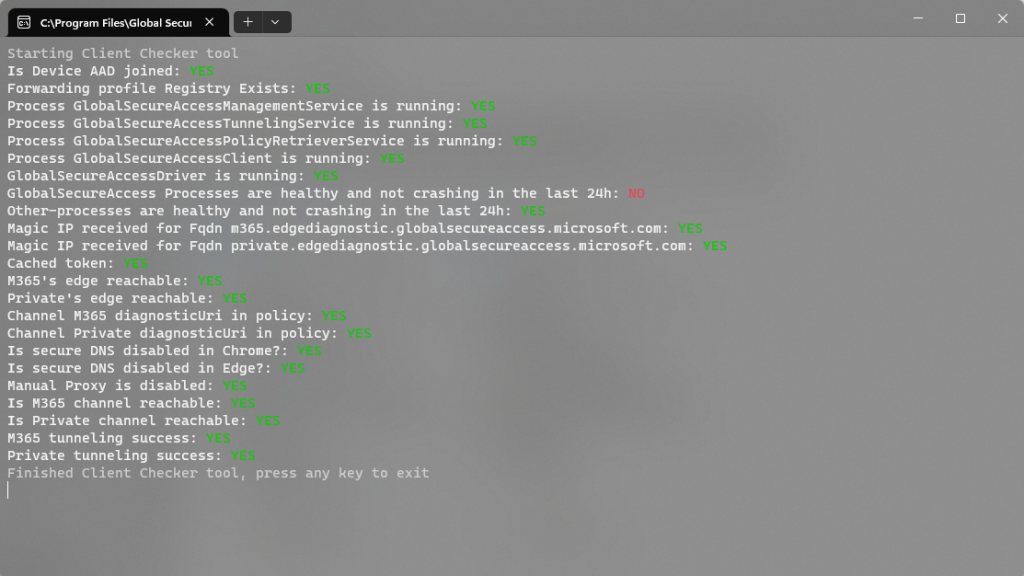
So let’s now check the Connection Diagnostics
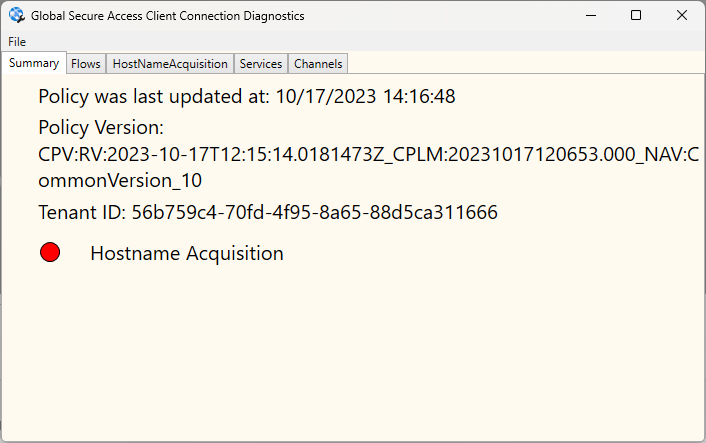
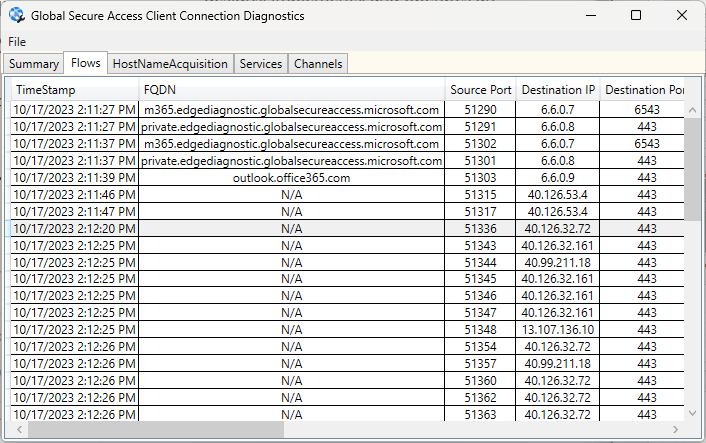
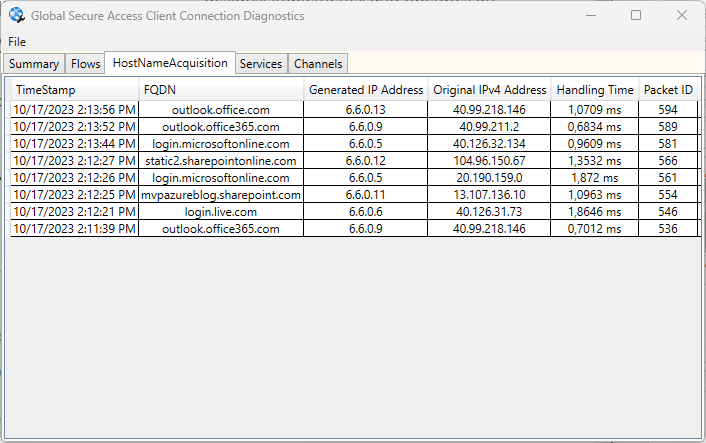
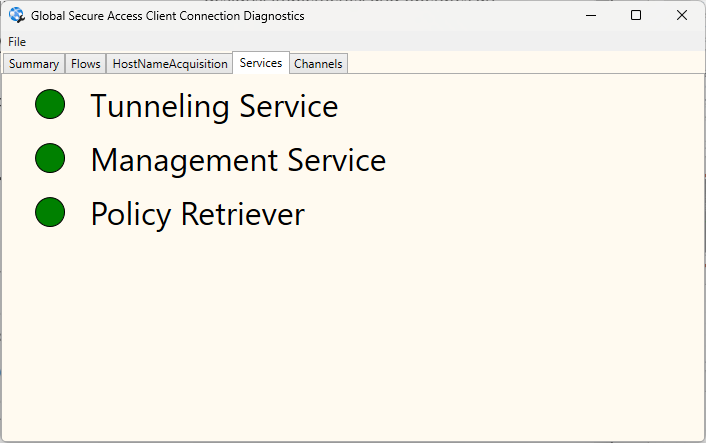
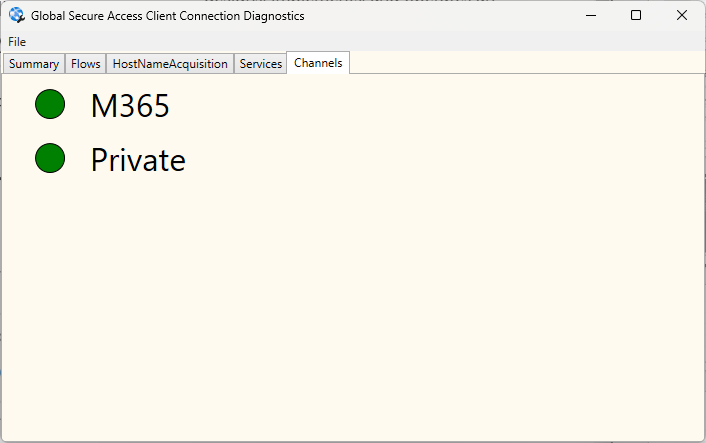
The most important thing is that we have green status next to the M365 channel meaning that communication to M365 services is secured,
So that would be it for now 🙂
In the next article, we will focus on Entra Private Access.
Comments are closed.